DoH with Quad9 DNS Servers

Updated July 25, 2019
We’re happy to announce Quad9 now has support for DNS over HTTPS (aka DoH).
DoH is a secure DNS protocol that is getting a lot of traction lately. Mozilla announced support for it in their Firefox browser and Google recently announced support for developers and Alphabet through Jigsaw released the Intra app for Android.
DoH is not supported at an operating system level therefore right now it requires the installation of additional software.
Already using a DoH client and want to test out Quad9? Use https://dns.quad9.net/dns-query
If you have an issue using the above query string please try: https://dns.quad9.net/dns-query?
We will be updating this post with additional configuration guides as they become available.
Additional Information
DoH requires either use of the system resolver or an IP address to perform the initial lookup for a hostname based query string. If you want to use the name to access it you need to be able to perform a lookup for that name. You can also point to the IP address.
Quad9 supports three flavors of DNS currently. A secured version, a unsecured or “vanilla” version and a version of our secured service that supports ECS.
| Service | DOH Address/Name1 | DNSSEC | Malicious Blocking | Encryption | IP Addresses |
|---|---|---|---|---|---|
| Recommended (Secure)2 | https://dns.quad9.net/dns-query | YES | YES | YES | 9.9.9.9, 149.112.112.112, 2620:fe::fe, 2620:fe::fe:9 |
| Secured | https://dns9.quad9.net/dns-query | YES | YES | YES | 9.9.9.9, 149.112.112.9, 2620:fe::9, 2620:fe::fe:9 |
| Unsecured | https://dns10.quad9.net/dns-query | NO | NO | YES | 9.9.9.10, 149.112.112.10, 2620:fe::10, 2620:fe::fe:10 |
| Secured w/ ECS support | https://dns11.quad9.net/dns-query | YES | YES | YES | 9.9.9.11, 149.112.112.11, 2620:fe::11, 2620:fe::fe:11 |
1: This is what you enter as the DNS server to use, exactly as shown. Be careful to not add a trailing ‘/ ‘after dns-query or your client may have issues connecting.
2: Our Recommend service is currently identical to our secure service, intended to be slightly easier to remember and more friendly for configuration. If you don’t know what to use, use this!
An easy way to test without changing anything in your favorite DoH client is to just perform the following query right from your browser:
https://dns.quad9.net:5053/dns-query?name=quad9.net
Updated 7/25/2019 – This is now running on a custom port since this implementation is not inline with the most recent standards based DoH implementation. (see RFC 8484)
You can also use the IP address instead of the name anywhere you see it when it comes to DoH – our certificates have all our common IPs, so this works too:
https://9.9.9.9:5053/dns-query?name=quad9.net
Updated 7/25/2019 – This is now running on a custom port since this implementation is not inline with the most recent standards based DoH implementation. (see RFC 8484)
Tested Client Implementations
- Intra (Android)
- DNSCrypt-proxy
- Firefox (Version 62 and later)
- Golang client and server
Additional client implementations and information can be found on (wikipedia).
Other Options for DNS Privacy and Encryption
Quad9 supports both DNS-over-TLS and DNSCrypt.
Configuration Examples
Intra
Download the Intra App for Android.
**Updated July 25, 2019. Quad9 is now included in the default list of DoH servers.
Launch the app and go to Settings:
Touch ‘Select DNS over HTTPS Server’:
Touch Built-in server and then Quad9 Secure DNS:
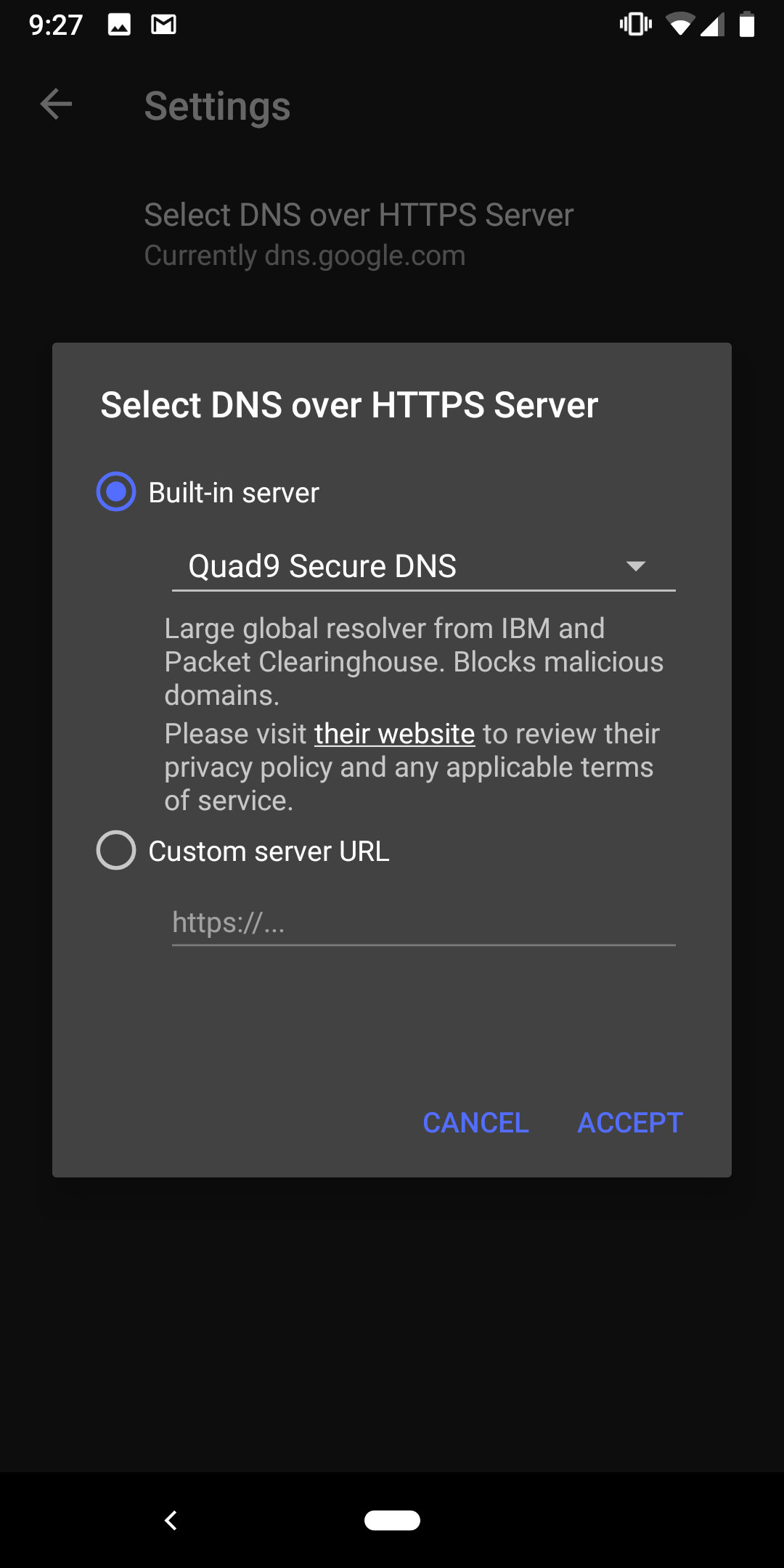
You will see the following confirmation screen and you need to touch ‘Accept” to apply your new settings:
For more stats and info scroll down:
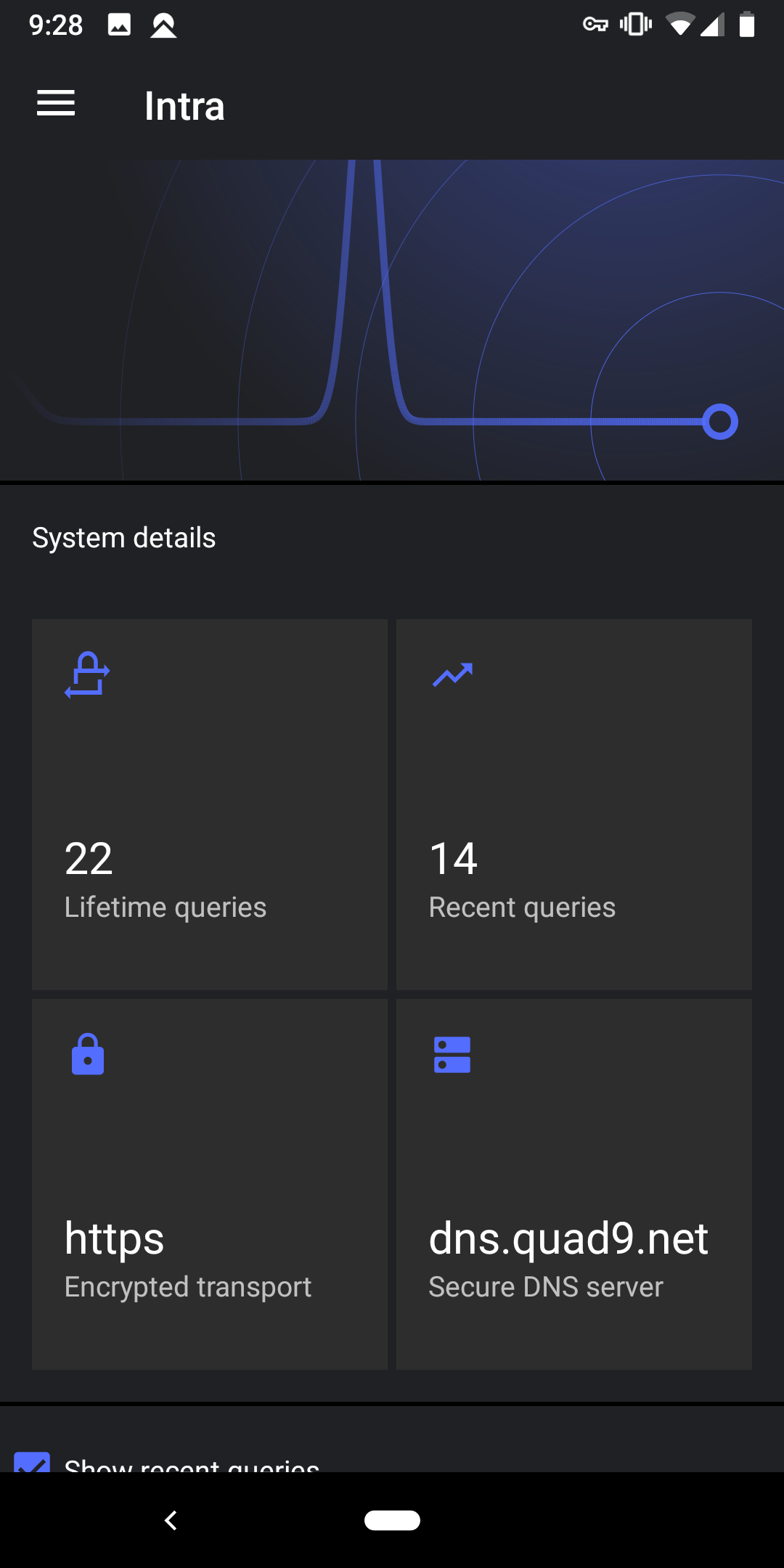
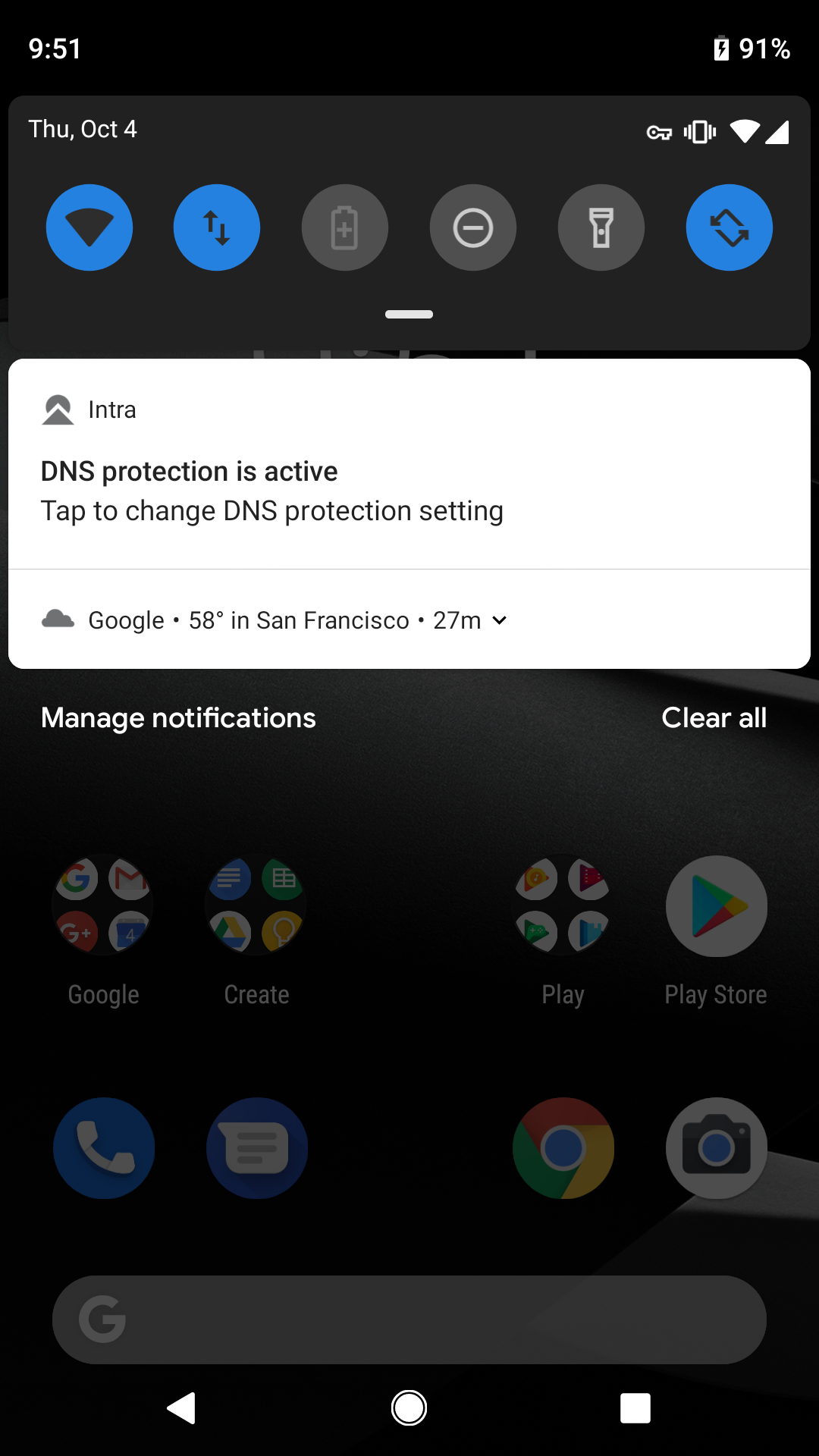
Once you exit the app you will see the following confirmation modal:
Firefox
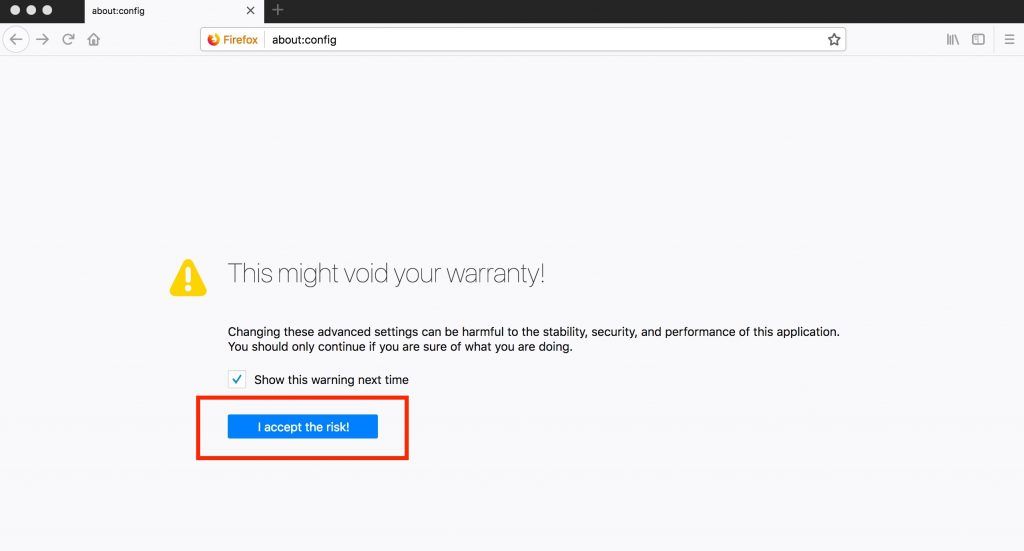
DNS over HTTPS (DoH) is not enabled by default, so you have to type about:config in your browser bar to open up the settings page.
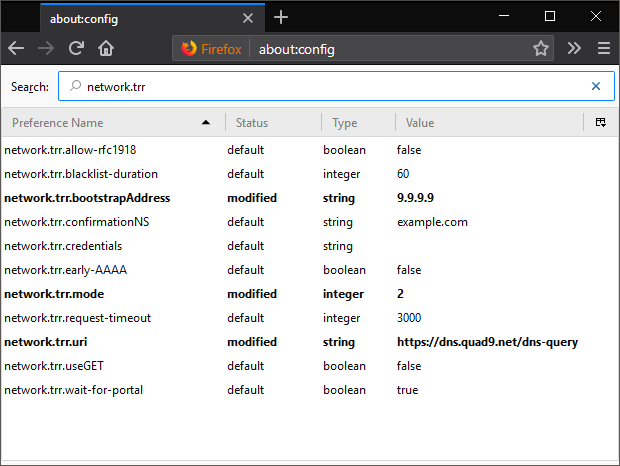
In Settings, you can modify 3 items related to the Trusted Recursive Resolver (aka network.trr):
-
network.trr.mode
-
trr.mode controls when and how DoH should be used. By default it is set to 0, meaning it is disabled. If you change it it will enable it.
- 0 — Off (default). To use operating system resolver.
- 1 — Race native against TRR. Do both in parallel and go with the one that returns a result first. Most likely the native one will win.
- 2 — First. Use TRR first, and only if the secure resolution fails use the operating system resolver.
- 3 — Only. Only use TRR. Never use the native (after the initial setup).
- 4 — Shadow. Runs the TRR resolves in parallel with the native for timing and measurements but uses only the native resolver results.
- 5 — Off by choice This is the same as 0 but marks it as done by choice and not done by default.
We recommend trr.mode of ‘2’ so it will fall back to the default resolver if the connection to the DoH server fails. If you only ever want to use DoH you can set it to 3 – You will be unable to resolve DNS names if your DoH server goes down and you won’t have a back-up using your system resolver.
-
-
network.trr.uri (this is where you specify the resolver you want to use)
-
network.trr.bootstrapAddress (you can forgo setting this and it will use the native system resolver for the initial query for https://dns.quad9.net/dns-query)
You can check out the logs by typing about:networking#dns into your browser bar. Look for TRR ‘true’ entries to see what is being looked up via DNS over HTTPS.


